Quick Links
Alchemy Mindworks Extended Security
What those mysterious registration keys do

This page will explain the current Alchemy Mindworks account and registration key security structure. It will also get into what the system is up to when it verifies an application, hopefully quelling any unseemly rumors that it's busy tweeting its friends behind your back.
For users of our software who are concerned about what it might be doing, we hasten to add that Alchemy Mindworks has been creating software since 1988 — over a third of a century. If we were going to embrace the dark side, we'd certainly have done it long ago.
Some History
 The previous generation of registration codes used by Alchemy Mindworks software — what we refer to as "second-generation security" — was born in the mid-1990s, a simpler and largely happier time. Our intent in creating that halcyon registration system was that it be easy to use, and not require that anyone jump through an unpalatable number of hoops.
The previous generation of registration codes used by Alchemy Mindworks software — what we refer to as "second-generation security" — was born in the mid-1990s, a simpler and largely happier time. Our intent in creating that halcyon registration system was that it be easy to use, and not require that anyone jump through an unpalatable number of hoops.
The level of security embodied in our second-generation registration code structure was a bit primitive, and we were under no illusions at the time that it would remain un-hacked. Our sense was that the cybercretins who stole our software would not have all rushed out to pay for legitimate copies of it, had they found themselves thwarted by impenetrable security. As such, there seemed little real purpose in making the registration code system unbreakable.
That was probably true at the time.
With the benefit of hindsight and introspection, our second-generation registration system was arguably a bit too trusting for its own good, and probably for ours. As we came to appreciate, there certainly were users who felt that stealing our applications was a workable alterative to paying for them. We began to get a sense of this when a growing number of them started requesting software support for them, using cracked codes to authenticate their accounts.
We've had software support requests from dead American presidents, all five Beatles, more John Smiths than can be found at even the most up-market bordellos, actors, musicians, athletes, historical figures and the always popular Zaphod Beeblebrox, who appears to own several hundred copies of Graphic Workshop all by himself.
Remarkably, some of them got decidedly stroppy when we declined to assist them. Hackers seem to feel that having gotten away with stealing intellectual property, they have every right to be treated just like real customers... in their dreams.
In more recent years, we've come to appreciate that we weren't the only ones getting ripped off when cybercretins warmed up their code cracking software. We've been contacted by several businesses who have bought significant numbers of licenses for our applications from parties claiming to be our distributors or resellers... all of which was installed with cracked codes. Some of them got a bit steamed when we explained that they'd been scammed, and that software support and upgrades would not be forthcoming for their purchases.
The coming of the great recession and the end of civilization as we know it greatly exacerbated the issues surrounding our second-generation registration system. Perpetually short on cash, a growing number of potential users of our applications decided that they'd use the software now and pay for it... whenever.
 Our sales began to tank, and the possibility that there would be no further upgrades to any of our products due to our impending corporate demise loomed increasingly large.
Our sales began to tank, and the possibility that there would be no further upgrades to any of our products due to our impending corporate demise loomed increasingly large.
Needless to say, we came to appreciate that a more robust security structure was called for. In practical terms, this meant maintaining a central on-line database of legitimate users, to which our software could refer to determine whether it was having its leg pulled when someone registered it. Even if hackers figured out how the registration keys worked, they wouldn't be able to get their cracked keys into the database.
A secondary benefit to this system was that it would allow our legitimate users to recover lost registration keys in a more secure and timely manner, and otherwise manage and fine-tune aspects of their users accounts interactively.
The catch in all this — and the reason you're probably reading this page — is that in order for our software to interact with the user database on our server, it has to access the Internet. In that rumor has it that genuinely nefarious software which lurks in the shadows and steals personal information also calls home over the 'net, someone is bound to question what the Alchemy Mindworks software that prompted you to read this page is really up to.
An explanation follows...
Calling Home
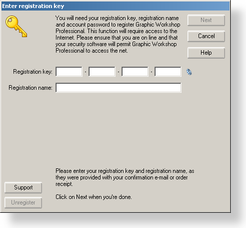 The current generation of Alchemy Mindworks software is registered with a registration key — we call 'em registration keys rather than registration codes now, as it seemed like a better metaphor when the current security system was being designed.
The current generation of Alchemy Mindworks software is registered with a registration key — we call 'em registration keys rather than registration codes now, as it seemed like a better metaphor when the current security system was being designed.
A registration key will look something like this — your key will differ from this example.
AB79C-NN36H-KL9TG-WL8R7
This is the sort of apparently meaningless string of characters that could only make sense to a computer.
A registration key references a registration name — typically, your name — which needs to match the key. As such, you'll have been provided with something like this when you registered one of our applications:
Graphic Workshop Professional 17 registration
Registration code for LANCELOT PIGSWALLOW: AB79C-NN36H-KL9TG-WL8R7
This assumes, of course, that your name is Lancelot Pigswallow, and that the appropriate office of your government was all out of the forms required to change it.
When you registered the software in question, we added an entry to the user database on our server that included your name, your registration key and your account password — something else you will have received when you registered the software.
When you enter your registration key in the software you licensed — that would be Graphic Workshop Professional in the foregoing example — the software will contact our server and confirm that your name and key are in fact in our database. When it receives notification to this effect, it will register itself and enable all its features.
The whole process takes about fifteen seconds.
As an aside, you'll be asked to select a secret question and provide an answer to it when you initially register your software. The account management function of your application will use your secret question and its attendant answer to verify who you are in the event that you lose your registration key at some time in the future.
When an Alchemy Mindworks application communicates with our server, it will send two short blocks of encrypted data that contain your registration name and key. They're encrypted so that if an intervening cybercretin manages to intercept them, he'll just make his head hurt trying to figure out what they mean.
We should also note that the database on our web server that the Alchemy Mindworks registration system interacts with is distinct from the database in our offices that holds customer information. The database on our server does not store credit card numbers, names and mailing address, telephone numbers or other significant personal details. Not that it's likely to happen, but in the event that hackers were to compromise our account database, the most damaging thing they could learn about you is that your first pet was a sloth named Petunia.
Evaluation Software
 If you install an Alchemy Mindworks software product for evaluation, you'll also get to interact with our account server... although in this case, you won't have to enter a registration key or choose a secret question. The software you're evaluating will access the Internet to call home and validate the product you're evaluating.
If you install an Alchemy Mindworks software product for evaluation, you'll also get to interact with our account server... although in this case, you won't have to enter a registration key or choose a secret question. The software you're evaluating will access the Internet to call home and validate the product you're evaluating.
Alchemy Mindworks software typically installs for evaluation with a ten-day trial period, during which time all its functionality is enabled and available for you to check out. When its initial evaluation period expires, some aspect of its functionality will be disabled. In the case of Graphic Workshop Professional, for example, the software will refuse to open higher-resolution graphics once its initial evaluation period has expired.
The process of validating evaluation copies of our software prevents the same product from being repeatedly installed, evaluated, uninstalled and then reinstalled to allow its fully-functional evaluation period to extend into the dimmest recesses of the future.
Once again, there's nothing particularly sneaky going on during the validation process for evaluation software. Two short encrypted blocks of data will be exchanged between the application in question and our server. Once your software has been validated, no further Internet activity will take place until its evaluation period has expired.
To the best of our knowledge, the longest recorded period of "evaluation" of one of our products was fourteen years. A user from Dallas, Texas contacted us in May of 2009 to register a copy of GIF Construction Set he'd download in 1995, and had finally decided was probably worth paying for. He, too, got a bit stroppy... in this case, when he learned that the registration cost had increased by five dollars in the intervening decade and a half.
As an aside, the mechanism by which our applications know whether they're being "evaluated" in perpetuity involves our database keeping track of the Windows machines they've previously been installed on. As such, if you evaluate one of our applications today and come back to evaluate it again in a few months, your second evaluation will consider itself to have expired. This will also be the case if someone has cloned your installation of Windows and installed an evaluation copy of the Alchemy Mindworks software in question — in which case you have a somewhat larger problem to concern yourself with.
In the event that you encounter one of our evaluation products that doesn't provide you with a full evaluation period — or any evaluation period — please get in touch with us. We can reset the appropriate field in our database.
Geo-Blocking
 One of the perennial issues we're called upon to address in running Alchemy Mindworks is the most effective application of our all-too-finite resources. When users with cracked codes attempt to obtain software support, for example, they occupy our support staff and prevent them from providing timely assistance to genuine users who genuinely deserve it.
One of the perennial issues we're called upon to address in running Alchemy Mindworks is the most effective application of our all-too-finite resources. When users with cracked codes attempt to obtain software support, for example, they occupy our support staff and prevent them from providing timely assistance to genuine users who genuinely deserve it.
When parties who are more likely to grow cranial antennae and tune themselves into satellite radio broadcasts than they are to actually pay for our products download great billowing swarms of our evaluation installers for no detectable reason, they frequently max out our servers and prevent our legitimate users from accessing the files they're after.
Regrettably, we've observed that a substantial portion of the abuse of our resources originates in specific countries. In most cases, our customer database indicates that over the past quarter of a century, we've sold precisely nothing to users located therein. It's entirely likely that this will continue to be the case for the next quarter of a century.
To better serve our genuine users, we've undertaken to restrict access to our products from places we're pretty sure no potential genuine users thereof exist.
We hasten to add that our geo-blocking strategy includes a mechanism for exceptions. If you've received a message to the effect that the product you've attempted to download or install isn't available in your location and you represent an identifiable government agency, academic institution or business, we ask that you accept our apology. Please get in touch with us and we'll unblock your access.
Bottom Line
 We created our current registration security structure because we have a serious commitment to our users. Not to put too fine a point on it, if we can't make enough money creating and maintaining Alchemy Mindworks' software products to keep our bookkeeper's head from exploding, we'll have to do something else.
We created our current registration security structure because we have a serious commitment to our users. Not to put too fine a point on it, if we can't make enough money creating and maintaining Alchemy Mindworks' software products to keep our bookkeeper's head from exploding, we'll have to do something else.
For the most part, non-existent software developers don't release a lot of product updates, or provide much user support.
As an aside, our bookkeeper — she of the exploding head mentioned earlier in this page — offered the somewhat draconian observation that anyone who doesn't trust us sufficiently to be comfortable with one of our applications validating itself over the Internet is cosmically unlikely to trust us with their credit card to pay for the product when they're finished evaluating it. We're not certain we wholly agree with this sentiment, but we usually listen to her because she has check-signing authority and the neatest handwriting in the company.
We'd like to take this opportunity to thank the many users of our products — during the development cycle for Graphic Workshop professional 4, the first of our applications to embed the new registration key functionality, we heard from hundreds of people who'd been using this software for a decade or more.
We'd also like to thank everyone who's been understanding about the realities of the new millennium, and our need for a registration process that can stand up to small minds and sticky fingers.
If you're reading this page in preparation for installing one of our products for the first time, thanks for checking out our software. You're about to join a very large family of users... and one with very deep roots. A quarter of a century has provided us with plenty of time to grow them.
Please contact us if you have any questions.
